Supra Simple Cybersecurity for Your Business

Cybercriminals are lurking around our data and becoming increasingly sophisticated in their burglary tactics. Adopting a multi-layered approach is key to keeping out these high-tech cyber bandits. In this article we’ll investigate the supra crucial importance of layering cybersecurity for your business and how it protects your organization from the ever-growing list of increasingly complex cyber sabotage techniques.
Size doesn’t matter when it comes to cyberattacks.
If you’re a small business owner you may think you are immune to cyber attacks. However, according to a report by Barracuda, average employees of small businesses (100 or fewer staff) get 350% more email attacks (specifically social engineering attacks that use impersonations or business email compromise) than those at a larger company.
Small Businesses get 350% more email attacks
Why are small businesses cyber attack targets?
According to the report, it’s because when you add up all the assets of a bunch of small businesses there’s a lot of value. Also, because they are small they have less security and expertise. It’s like fishing (not to be confused with phishing, but phishing is included in their tactics) – catching a big muskie is harder and more time-consuming than catching 15 bluegills.
$2.4 billion
Total cost of cybercrimes to small businesses in 2021 (fbi.gov)
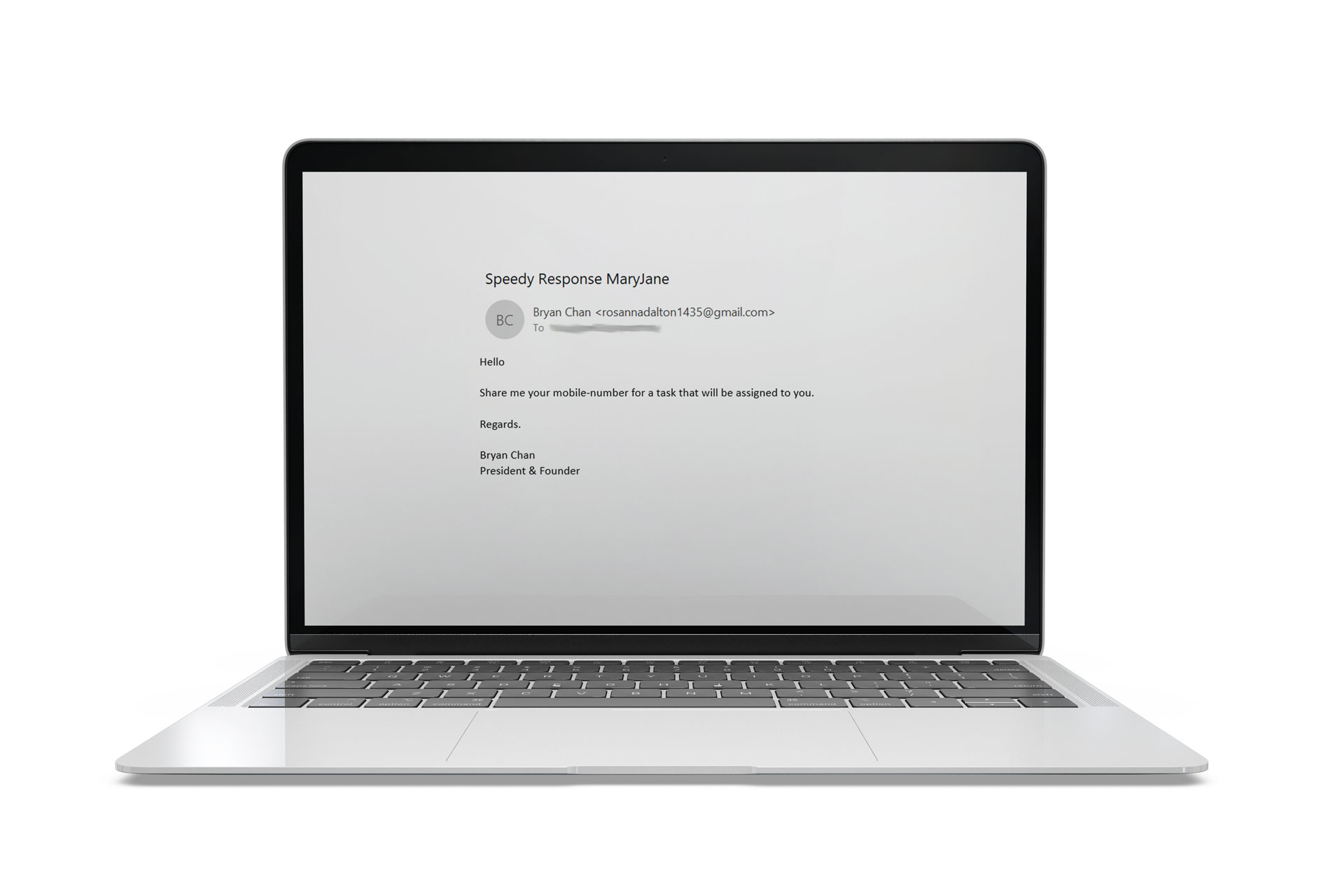
Cyber criminals’ methods are becoming more targeted and psychological. Consequently, traditional digital security operations no longer cut it. For example, criminals get into the company email system. (More sophisticated than the phishing email above.) They send fake emails to employees that look like they are coming from their boss or another C-Suite executive in which they request gift cards, wire transfers, or other questionable actions regarding money transfer. Additionally, they impersonate vendors and infiltrate business conversations via email in a tactic known as Conversation Hijacking.
Of course, hackers also try to take on the identity of trusted brands and send bogus security alerts. The main goal is to have the target enter their credentials and use them to access company network information.
According to the Barracuda report the top 10 brands hackers impersonate are:
- Microsoft – 57%
- WeTransfer – 17%
- DHL – 6%
- USPS – 5%
- DocuSign – 3%
- LinkedIn – 3%
- eFax – 2%
- Instagram – 2%
- Apple – 1%
- Google – 1%
As a response to these growing challenges, cybersecurity experts suggest a multi-faceted approach known as a “layered defense.” This approach consists of a series of security measures, each adding an additional barrier that an attacker must overcome.
You will find different words, order, and even methods for defense. Here are our suggestions to help you stay safe.
Layers of Cyber Security
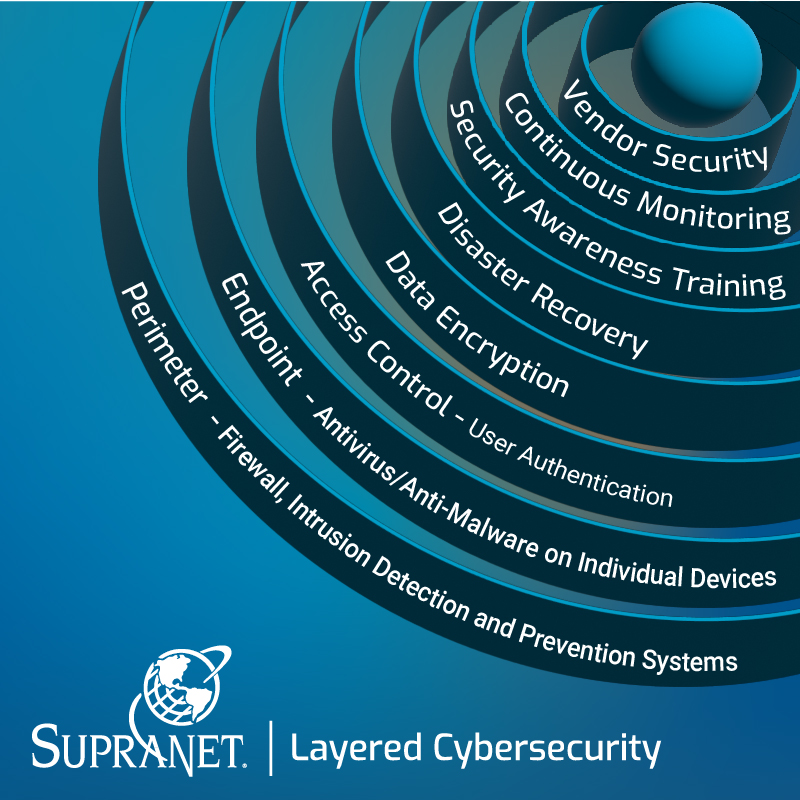
Perimeter Security – This is your first line of defense, usually consisting of personal firewalls (check out the best of 2023 here from TechRadar), hardware firewalls intrusion detection (IDPS) systems, and intrusion prevention systems. These types of software security programs filter incoming and outgoing network traffic. They act as a digital fence, preventing unauthorized access to your network.
For a list and reviews for SMB IDPS, check out this list on G2.
Personal Firewall vs Hardware Firewall
A personal firewall resides on the end user’s computer or other devices. It can detect harmful traffic passing in and out. If malware does make it onto your computer, a personal firewall can alert you if it tries to attack others on your network.
Think of a hardware firewall as a digital security guard for your entire network, not just one computer. It’s a physical device, like a specialized box or router, placed between your internet connection and your business computers. Unlike software firewalls, which are installed on individual machines, a hardware firewall protects your entire network by filtering incoming and outgoing data, acting as a barrier against cyber threats. It’s typically set up by connecting it to your network infrastructure, creating an extra layer of defense against online dangers.

“Despite the similar names, a hardware and personal firewall should not be considered an either-or, but complementary products.” – Colin Baker, Senior, Senior Network Engineer, SupraNet
Endpoint Security – First off, what’s an endpoint? Computers, smartphones, tablets, printers, servers, medical devices – literally anything that connects to your network and someone uses is an endpoint.To secure these devices you install antivirus software, anti-malware tools, and encryption to safeguard data. For more information on the types of Endpoint Security, check out this article from Fortinet.
Access Control – This layer ensures that only authorized users have access to your systems and data. It involves user authentication, role-based access control, and strong password policies. Implementing multi-factor authentication (MFA) can significantly enhance access control.
Data Encryption – Data is often the primary target of cyberattacks. Encrypt sensitive data both in transit and at rest to ensure that even if an attacker gains access to it, they won’t be able to decipher it without the encryption keys.

Security Awareness Training – The human factor is often the weakest link in cybersecurity. Training employees to recognize phishing attempts and follow security best practices is crucial in preventing social engineering attacks. (For example, remember the brand impersonations? Tell your staff to be very wary of emails that look like they are coming from Microsoft.)
Incident Response and Disaster Recovery – Despite the best preventive measures, incidents can still occur. This layer involves having a robust plan in place to detect, respond to, and recover from security breaches. Regularly testing this plan is essential.
“An increasingly common security breach is ransomware, where an attacker will encrypt your data and render them unusable, offering to unlock them for payment. A regular backup schedule for any data that cannot easily be replaced by a full reinstall is critical. Along with backups, restoration procedures must be tested regularly as part of your disaster recovery plan,” suggests Baker.
Network Monitoring and Intrusion Detection – Continuously monitoring your network for suspicious activities and using intrusion detection systems can help identify threats in real-time, allowing for a faster response.
Vendor and Supply Chain Security – Third-party vendors can introduce vulnerabilities to your systems. Evaluate your third-party vendors’ security practices and ensure they meet your standards.
Software Updates – Your software vendors will provide regular updates when new vulnerabilities are discovered. Work with your vendors to be sure you are notified of updates, and apply them ASAP.
The Benefits of Layered Cybersecurity
If you’re business is small, medium or large, by implementing multiple layers of cybersecurity, you will benefit in several ways:
Defense in Depth – Attackers must navigate through multiple barriers, making it more challenging for them to infiltrate your systems.
Early Detection – With multiple layers in place, you are more likely to detect and respond to threats before they escalate into major breaches.
Reduced Attack Surface – Each layer reduces the potential vulnerabilities, minimizing the attack surface available to malicious actors.
Adaptability – As the threat landscape evolves, having multiple layers allows you to adapt and add new security measures as needed.
Relying on a single cybersecurity solution is no longer sufficient. By implementing a multi-layered approach, you build a robust defense against the ever-changing landscape of cyber threats. Remember, cybersecurity is not a one-time effort but an ongoing commitment to protecting your organization’s valuable assets and maintaining the trust of your customers and clients.




